Virtual Private Network

Virtual Private Network or VPN allows people to browse securely via an array of encrypted services that allow masking of individual identities. Users gain access to websites that are banned or those that are available in specific countries. VPN allows two or more networks to connect. Companies can allow access to their servers by their employees to work remotely using unsecured or public internet connectivity.
The VPN network is completely off radar from the internet. Businesses, government organisations, military make use of them to send and receive confidential information securely. For example, if one has a VPN connection on their home computer, with one click they can connect to a private server anywhere in the world. The VPN masks the IP address by using a proxy.
The VPN technology pose a great threat to the national security; hence the Home Affairs Committee has urged the Indian government to impose a permanent ban on VPN across the country with regards to security. Cyber infrastructure has seen a tremendous growth worldwide, especially in India in the last five years. Remote functioning capabilities are advancing with an accelerating speed which in turn poses sever threats to the cyber security walls especially when criminals can remain anonymous.
The IP address
IP stands for Internet Protocol. Just like we have our postal addresses that identify our location; IP address is a numerical tag that identifies a device connected on the internet. The IP address can reveal information like city, pin code, internet service provider’s name and area code etc. It is an online unique identification code that can geolocate an individual. Every device connected to the internet has access to the world wide web (www), thus, all of them have an IP address in order to communicate with the internet.
For instance, navigate to the browser and type “What’s my IP?” (Figure 1). The internet returns your IP address as results. Next, connect to the VPN; for demonstration we have connected to New York, USA. Once connected, search for “What’s my IP?” and see the results in (Figure 2). The IP address has changed. Knowing someone’s IP address does not directly reveal the user’s personal information, neither does it geolocate the device address. However, information can be pieced together to form a bigger picture of your online activities.
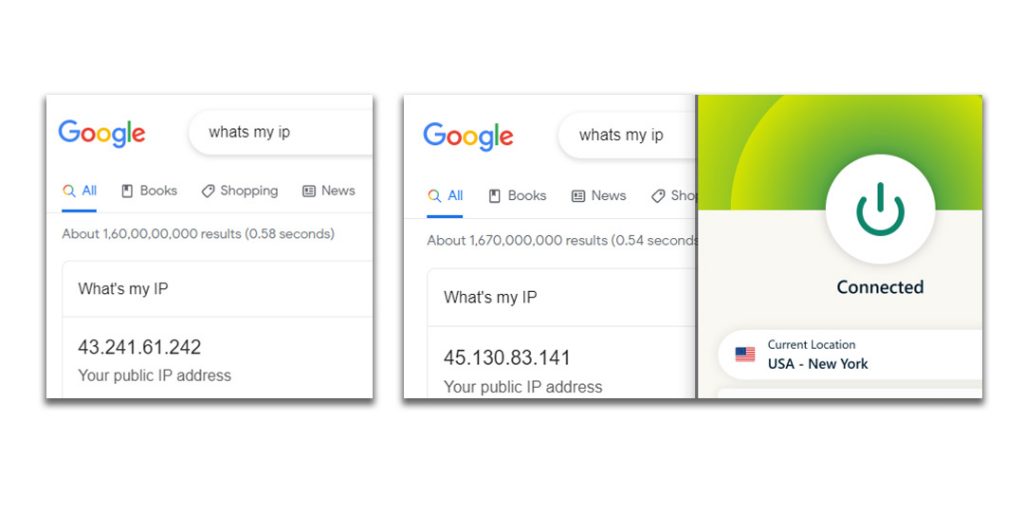
If the internet service provider is known, the area code is known then it becomes easier for the law enforcement agency to gather more evidence from them about the suspected IP address. On the contrary, if one buys a VPN subscription and makes payment with a credit card, information can be traced back to the bank details and eventually to the registered address of the individual. However, this can happen only if the law enforcement has court orders, and the VPN service provider cooperates in events of crime. Nevertheless, payments made using anonymous modes like bitcoins can obliterate an investigation.
The brighter picture
Virtual private network has eased the way in which remote working is functioning today. Companies are able to allow their employees to login to the company network from anywhere in the world. The data is also secure since it is a part of an encrypted network. Additionally, VPNs allow sharing of information in a secured tunnel from the sender to the receiver. It is very crucial when it comes to sharing of information by government agencies, military, and business entities.
VPNs block access to third parties that collect user data to promote their ads. On the bright side, VPN is a tool that secures communication and interactions with the internet. Like every other technological implication, VPN too has a darker side. It is an ongoing debate whether the negative repercussions outweigh the positives a VPN carries.
In order to remain anonymous, public Wi-Fi can be used. But it is not a secure form of using the internet, these networks can be easily hacked.
VPN: Disguise | Anonymity | Underground world
These are widely used to browse through hidden websites like pornography sites called Pornhub that are banned in the country (Pandey and Sharma, 2019). When PUBG was banned in India, it was taken off from all app stores and websites were blocked. VPNs like that of Nord, Express and IP Vanish became massively used to download the app from the official website.
PUBG mobile is still functional in India despite the ban by the Indian government. After the APK file is downloaded and the resources have been installed, VPN is not required to run the game. Users faced no issues in connectivity and execution, they were also able to update the game to latest configurations (Mukherjee, 2021). It is important to note, that PUBG was banned on the grounds of tampering the right to privacy and was perceived as a threat to national security (Minocha, 2019).
India’s Personal Data Protection Bill, 2019 is influenced by global developments in the cyber space. It is inspired by the GDPR (General Data Protection Regulations, EU) (Suryavanshi, 2019). The GDPR has blocked access to sites that are non-compliant to the regulations and returns an error: “This content is not available in your area” or “We recognize you are trying to access this website from a country belonging to the European Economic Area including the EU which enforces the GDPF and therefore cannot grant you access at this time” (BBC News, 2018). India, too has blocked sites and applications like TikTok, Share it, Shein etc. However, these can be accessed with the help of a VPN.
VPNs are used to access to the underground world of the internet. General internet users usually have access to merely 5% called the surface or the visible web where search engines like Google, Yahoo, Bing etc. can crawl and index information and web pages. Remaining 95% of the iceberg is dominated by the deep and the dark web. Here, one can gain access to important data, government records, sensitive information, illegal activities, counterfeit related services and can even hire a hitman (Godawatte et al., 2019; Jolley, 2021; Weimann, 2015).
The technology enables sharing of illegal files, files that do not belong to the user and are prohibited from sharing such are movies, videos, songs, or commercial software’s. Thus, amounting to copyright infringement. Some data could be restricted from sharing or simply be illegal like pornography or videos showing extreme violence and immoral acts like rapes and murders. Moreover, stalking on the internet disguised in new avatars creates more nuisance in today’s world. Cyberstalking is illegal in almost all parts of the world.
Cybercriminals and hackers use VPNs to commit various types of cybercrimes like installing a malware or ambush the victim’s network with a denial-of-service attack. It may be of particular interest to identify where an email is being sent from to initiate a transfer from the bank or whether the location of your employee is consistent to what is being said.
But, like VPN, the dark web also has legitimate purposes. Individuals have access to a whole new world of information, scientific journals, books etc. Users can share information anonymously about happenings in the country or report crimes without the fear of being spied upon.
VPN, India, and the problem
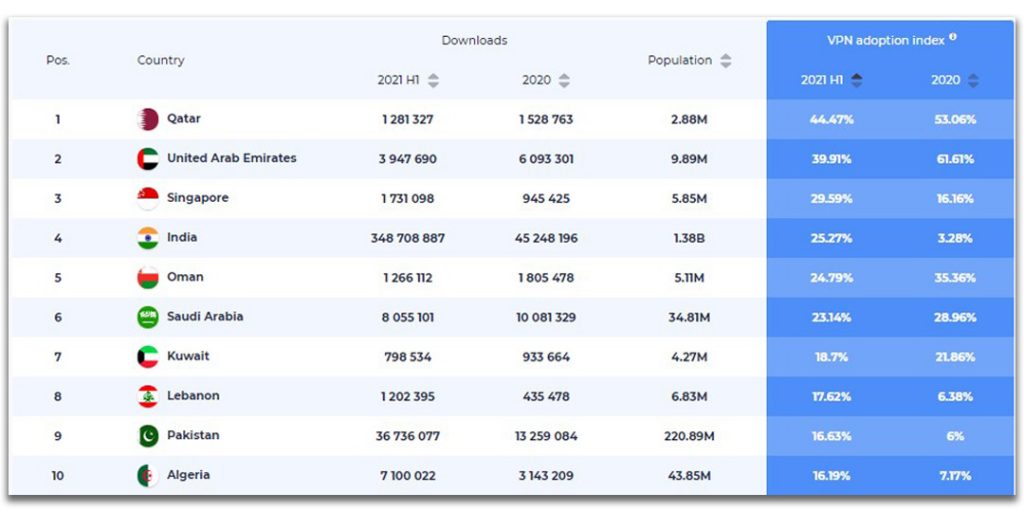
According to the global VPN index, India is amongst the top four countries with maximum VPN downloads and adoption rate in the first half of 2021 (figure 3). The VPN download rate in India has multiplied seven times in the first half of 2021 than the year 2020.
It becomes highly impossible to identify criminals because their identities are disguised. Threat actors avoiding surveillance is a matter of concern for the government authorities because tracking their activities becomes difficult. Law enforcement agencies have to resort to more extensive methods of tracking criminal activities online.
The ease with which a VPN subscription is available is another stumbling block. Free VPN providers like Proton VPN, Tunnel Bear, Hotspot Shield etc. are free solutions for beginners. However, “Nothing comes for free”, free software could come with a malware (Deloitte, 2020), or they could embed third party trackers in their tool to track your online activities. Data collectors sell user data to advertising agencies who can target you with customized ads or they can even sell your data to others. Premium versions aren’t very expensive, they come with a list of promises to secure your identity and may give value to your privacy.
A VPN connection can also be subject to a man-in-the-middle attack (MTMA) if poor authentication mechanisms are present. MTMA is referred to as eavesdropping, a cybercriminal can get in between and spy on the data sent from one device to the server. It can appear to be legitimate to both the sender and the receiver and can interrupt conversations, steal data, or affect transfer of data. However, this kind of an attack can even happen without a VPN!
The parliamentary committee recommends that the Ministry of Electronics and Information Technology must identify and block VPN services with the help of the internet service providers. A coordination mechanism with the Ministry of Home Affairs and the International agencies would open doors to increased censorship. It could also enable blocking of social media apps like WhatsApp, Telegram, Twitter, Instagram, and Facebook.
Cybersecurity concerns are intrinsically linked to national security. VPN providers in turn have access to the sensitive government information through their software. When the locations of the VPN servers are situated outside the country, the tool directs all the user traffic through their servers. National security is compromised if the location of these servers are in countries that do not share values and similar interests to that of India.
Moreover, VPN providers can take advantage of housing our data with a malicious intent. A journal articles quotes, “a warning issued by the Indian government that the Chinese government is using their VPN applications to collect user data” (Alashi and Aldahawi, 2020). Thus, leading to issues of cyber spying on the state or the country. There may be threats of political, cultural, social, and economic nature.
Ban or no ban?
VPN providers are required to maintain connection and browsing logs. It is a comprehensive report about user activities, their communications, and other intrinsic details (Verizon, 2020). The connection logs include name, email address, time stamps and the IP address typically. It may also include payment details if a credit card has been used. Without logging these details, the service providers wouldn’t be able to manage the account expiry details of the users (Williams, 2021).
The government of India can establish agreements with VPN service providers with conditions on ‘access to information’ will help in the long run. It implies that user information and activities must be readily provided by the VPN companies to the law enforcement agencies on court orders.
The providers located in the US, EU and the UK are legally required to maintain these logs and produce them upon court orders. Could India negotiate a regulated framework that sustains legitimate use of a VPN and at the same time mandates illegal use. On the contrary, it compromises the entire concept of having an anonymous and secure network for privacy. Also, wouldn’t it be an offence to keep browsing logs of users without their consent? Here, there is a very thin line between right to privacy and right to information.
While virtual networks are invisible, detection infrastructure can be developed which will help the government to monitor traffic from the VPN servers. The IP addresses of VPN servers need to be regulated all over the world. Therefore, it is vital to detect these servers and create a database, for example, if an email has been sent using a VPN, the receiver sees an alert marked in the mail automatically. Furthermore, a global pact amongst these nations can help to provide information legally across borders.
Currently, Information Technology Act, 2000 governs the cyber laws and the data protection laws of the country. Additions or amendments to the law with deterrent measures like strong fines and imprisonment can be imposed on criminals that use the VPN services with a malicious intent or the ones that use them without the government’s authorization.
There are laws that punish individuals who download unauthorized content from the internet like a movie or other forms of entertainment however, with a VPN, chances of being caught for petty crimes are close to impossible. It is absolutely legal to use a VPN in India, there are no laws that restrict its use as long as there are no illegal activities committed with it (Norton, 2021).
Other countries
A handful of countries have an outright ban on virtual private network, or have regulated its use with appropriate censorship laws. To name a few, China, North Korea, Turkmenistan, Uganda, Belarus, Oman, Russia, Iraq, Turkey, and the UAE have imposed these restrictions.
Russia | Belarus
Russia has completely banned VPN in 2017 in an attempt to increase the governments control over the internet and citizen data (Goryachev, 2017). Known VPN service providers have been blacklisted in the country. Similarly, Belarus banned the technology in 2016 with additional block to the right of free speech enforced upon its citizens.
Iraq
Iraq banned the use of VPNs permanently in 2014. The ban was a result of tracking and stopping ISIS from exploiting the social media platforms. Any attempt to access the home page of a VPN service provider would automatically be terminated by the internet service providers (Alashi and Aldahawi, 2020).
UAE
The United Arab Emirates have tightly regulated the use of VPNs. A penalty of not less than one hundred and fifty thousand dirhams (approximately 30,00,000 INR) and not more than five hundred thousand dirhams ( approximately 1,00,00,000 INR) is imposed on criminals who mask their identities with a VPN to commit frauds and other crimes. The UAE Telecommunications Authority pointed that there are no regulations to prevent the use of VPNs in institutions, companies, and banks for access to their internal networks (STA Law Firm, 2018).
Oman
The Sultanate of Oman forbid the use of any form of encryption technology without the permission from the government in 2010 (Alashi and Aldahawi, 2020). A licence from the Telecommunications Authority is required for commercial use by individuals and organisations.
China
China controls the internet available to their citizens, hence, it has achieved cyber sovereignty within its borders regarded as the ‘Great Fire Wall’. The government has blocked access to networking sites like Google, Facebook, Twitter, and others so that the political parties do not use it as a battlefield and the information remains within closed borders. The Chinese firewall has also blocked media portals, porn sites, search engines and VPNs (Chandel et al., 2019; Normile, 2017).
However, if one downloads and installs the tool from a premium service provider (like Express VPN, Surf shark, Astrill VPN and Private VPN) before arriving in China, he can have access to the VPN. There are other ways to using a VPN in China such as identifying new service providers with new IP addresses that aren’t blocked can help to bypass the firewall. Hence, we could say that China has tightly regulated the use of VPN technology in the country.
China has been in the race to control the way companies access the internet in the country. The government wants these corporations to use government registered VPNs to protect their data which looks petrifying because then the government has access to their data.
Conclusion
VPN is legal in some countries while some have completely banned or tightly regulated its use. There could be possibilities of banning VPN in India but not entirely. The government must focus on regulating deals with VPN services providers with access to information without long hauls and even tiring processes on criminal issues.
Spontaneously responding to requests from the law enforcement and making important disclosures can help in fast forwarding investigation processes. Failure to produce browsing logs and connection logs would result in cancellation of licences for the VPN provider. Imposing deterrent laws with heavy fines for unauthorised use of virtual private networks will help to stabilize anonymity over the internet. Illegal services on the dark web need extensive monitoring. Other ways of investigating networks of illicit chemicals, arms and ammunitions, drugs etc. need to be explored.
Banning VPN services alone will not help in prevention of cybercrime. Even if the government plans on banning the VPN, making sure that “the ban is doing what it is meant to do” is important. It would be nothing less than a cat and a mouse game where the government is adding restrictions and users are finding more sophisticated ways to bypass those limitations. Law enforcement agencies can use court orders to gather information from internet service providers, server logs of VPN service providers as well as websites and mobile applications.
There is a strong need for regulation, of course there needs to be updated laws that enhance the fight against cybercrime and anonymity. Like most other countries, India is not against the use of a VPN. But, to combat cybercrimes emerging due to anonymity needs to be dealt with. The question is: Do the negative repercussions of the VPN technology outweigh its positives? Will the ban by the Indian government materialize its intentions?
References
Alashi, S. and Aldahawi, H. (2020) ‘View of Cybersecurity Management for Virtual Private Network (VPN) Applications: A Proposed Framework for the Governance of their Use in the Kingdom of Saudi Arabia’, Journal of Information Security & Cybercrimes Research, 3(1), pp. 31–57. Available at: https://journals.nauss.edu.sa/index.php/JISCR/article/view/1226/958 (Accessed: 4 September 2021).
BBC News (2018) GDPR: US news sites unavailable to EU users under new rules – BBC News., BBC News Available at: https://www.bbc.com/news/world-europe-44248448 (Accessed: 4 September 2021).
Chandel, S., Jingji, Z., Yunnan, Y., Jingyao, S. and Zhipeng, Z. (2019) ‘The Golden Shield Project of China: A Decade Later-An in-Depth Study of the Great Firewall The Golden Shield Project of China: A Decade Later An in-depth study of the Great Firewall’, International Conference on Cyber-Enabled Distributed Computing and Knowledge Discovery (CyberC) Available at: 10.1109/CyberC.2019.00027 (Accessed: 4 September 2021).
Deloitte (2020) COVID-19’s Impact on Cybersecurity. Deloitte. Available at: https://www2.deloitte.com/content/dam/Deloitte/ng/Documents/risk/ng-COVID-19-Impact-on-Cybersecurity-24032020.pdf (Accessed: 03 September 2021).
Godawatte, K., Raza, M., Murtaza, M. and Saeed, A. (2019) ‘Dark web along with the dark web marketing and surveillance’, Proceedings – 2019 20th International Conference on Parallel and Distributed Computing, Applications and Technologies, PDCAT 2019, Institute of Electrical and Electronics Engineers Inc., pp. 483–485.
Goryachev, I. (2017) ‘Russia Introduces New Rules On VPNs And Anonymisers – Media, Telecoms, IT, Entertainment – Russian Federation’, Mondaq Available at: https://www.mondaq.com/russianfederation/it-and-internet/640542/russia-introduces-new-rules-on-vpns-and-anonymisers (Accessed: 4 September 2021).
Jolley, D.W. (2021) ‘If You Only Knew the Power of the Dark Web! Finding Intellectual If You Only Knew the Power of the Dark Web! Finding Intellectual Freedom, Privacy, and Anonymity Online Freedom, Privacy, and Anonymity Online’, Digital Commons @ Gardner Webb University Available at: https://digitalcommons.gardner-webb.edu/doverlibfacpub/18 (Accessed: 4 September 2021).
Minocha, A. (2019) PUBG and The Right To Privacy: Drawing A Contrast Between the Contemporary Ban., Legal Service India Available at: https://www.legalserviceindia.com/legal/article-4538-pubg-and-the-right-to-privacy-drawing-a-contrast-between-the-contemporary-ban.html (Accessed: 4 September 2021).
Mukherjee, A. (2021) PUBG Mobile global: What happens now if you install it in India via VPN?., BGR Available at: https://www.bgr.in/gaming/pubg-mobile-global-india-vpn-download-apk-gameplay-battlegrounds-mobile-launch-date-959232/ (Accessed: 4 September 2021).
Normile, D. (2017) ‘Science suffers as China plugs holes in Great Firewall’, Science, 357(6354) American Association for the Advancement of Science, p. 856.
Norton (2021) Are VPNs Legal or Illegal?., Norton Available at: https://in.norton.com/internetsecurity-privacy-are-vpns-legal.html (Accessed: 4 September 2021).
Pandey, S. and Sharma, D.H. (2019) ‘Blocking Mechanism of Porn Website in India: Claim and Truth’, Cornell University, 7 Available at: https://arxiv.org/abs/1906.10379v1 (Accessed: 4 September 2021).
STA Law Firm (2018) ‘Law Governing VPNs – Media, Telecoms, IT, Entertainment – United Arab Emirates’, Mondaq Available at: https://www.mondaq.com/it-and-internet/765728/law-governing-vpns (Accessed: 4 September 2021).
Suryavanshi, H. (2019) ‘India’s Personal Data Protection Bill (“PDP Bill”), 2018: Brief Introduction, Key Provisions and Comparison with GDPR’, International In house Counsel Journal, 12(47)
Verizon (2020) Data Breach Investigations Report. Available at: https://enterprise.verizon.com/resources/reports/2020-data-breach-investigations-report.pdf (Accessed: 2 September 2021).
Weimann, G. (2015) ‘Going Dark: Terrorism on the Dark Web’, http://dx.doi.org/10.1080/1057610X.2015.1119546, 39(3) Routledge, pp. 195–206. Available at: 10.1080/1057610X.2015.1119546 (Accessed: 4 September 2021).
Williams, J. (2021) Do VPNs Hide/Block My Search History? (Explained!)., Techpenny Available at: https://techpenny.com/vpn-block-search-history/ (Accessed: 4 September 2021).



