Digital Forensic Investigation Capabilities for first responders

By Dr. Vinod Surana
Prevention and Response Checklist for Victims and Investigation Agencies
Introduction to Digital Forensic
A Singapore based cyber research firm has alerted the Indian cyber agencies about a massive cyber-attack by a Chinese hacking group from June 21, 2020 onwards (Mirror now, 2020). The targets are believed to be ministries, firms, IT sectors and media houses in Delhi, Kolkata, Ahmedabad, Mumbai and Hyderabad. A splurged movement on the dark web, manifesting an increase in aggression by these attackers are noticed post the geopolitical clashes in Galwan at the Ladakh border.
India’s Computer Emergency Response Team (CERT-In) has unfurled red flags against information theft and intellectual property theft by means of an opportunistic phishing attack in view of the pandemic (Chattopadhyay, 2020; Indian Computer Emergency Response Team, 2020). Section 69 of the Information Technology Act, 2000 of India empowers CERT-In to issue directions for monitoring the traffic and decryption of information as required (India code, 2011). These attacks come with an intent to threaten the security, integrity and sovereignty of India, thus introducing contamination to the digital devices as stated under section 66f of the IT Act, 2000 of India (India code, 2011).
The cyber criminals claim to have about 2 billion email id’s belonging to Indian citizens. The Covid-19 situation has already weakened the backbone of the Indian economy as well as had mental implications on many. Remote setups have skyrocketed cyber threat possibilities where users lack critical IT infrastructure and use online tools for team interactions. According to Kaspersky Security Network, India has seen a sudden surge in cyber-attacks by 37% in the beginning of 2020 as compared to the end of the previous year (CisoMag, 2020). Cyber-attacks using Covid-19 as a decoy would cause paramount destruction.
Modus Operandi digital forensic
Cyber criminals send phishing emails to potential victims impersonating the decision makers of the government (figure 1). The content of the email is relevant to the latest updates regarding Covid-19 for example: “free Covid-19 tests” enticing the victim to register. The registration link redirects to a malicious website that collects the user’s sensitive personal information and financial details (Indian Computer Emergency Response Team, 2020). This part of the attack lands the user to a legitimate looking site in order to avoid suspicion (Lazar, 2018).
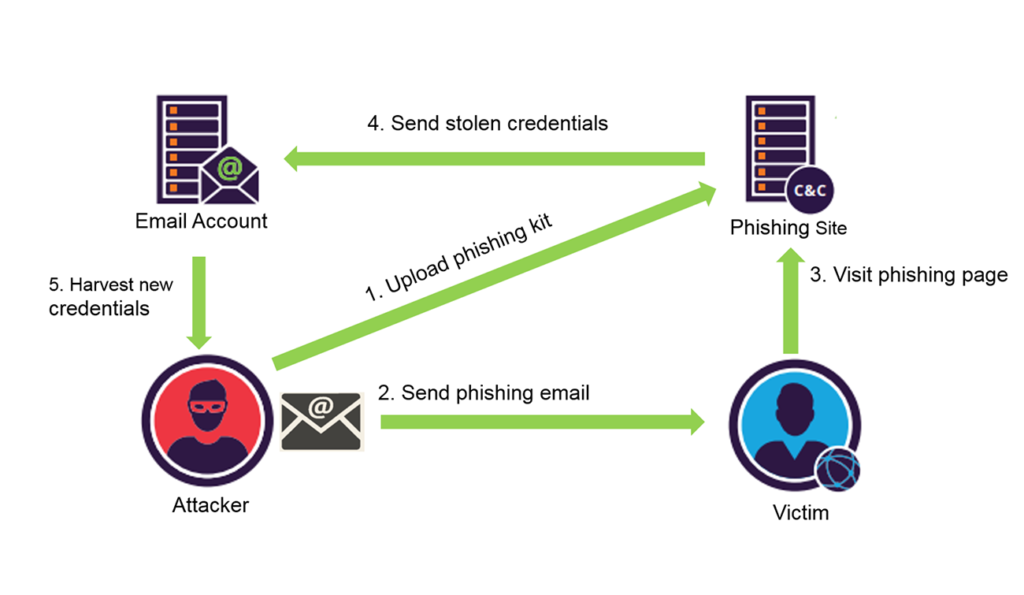
Figure 1: How a phishing email gather sensitive information from you (Lazar, 2018).
Similar emails may be backed by Coronavirus-themed malware attachments. When the user downloads this attachment, their device is infected by a malicious code which infiltrates into the system. The malware attack steals the victim’s personal information and has capabilities to spy on the victim without their knowledge (Indian Computer Emergency Response Team, 2020).
The emails are likely to originate from spoofed email id’s resembling “gov.in” domains, example: “ncov2019@gov.in”. The attacker sends IP packets from a false IP address disguising itself or by targeting the original IP address of the firm and sending packets from the real IP to many others in the network. Spoofed emails are difficult to investigate because the domain often links us to the original website instead of the impersonated. The core email protocols, do not have authentication mechanisms to identify spoofed email ids thereby landing in our mailbox. In 2019, 94% of data breach attacks delivered malware by email (Verizon, 2020).
A Threat to India digital forensic
Various sectors in India have been targeted since 18th June 2020, Maharashtra’s cyber security cell reported an upswing of over 40,300 cyber-attack attempts (200% rise) made within just five days (Sahay, 2020). The origin of a major chunk of these attacks stem from Chengdu, capital of China’s Sichuan province. Sichuan is the headquarter for China’s Cyber-warfare. Amongst the many attacks, Distributed Denial of Service (DDoS), IP Hijacking and Phishing are the most prevalent ones. Malware including Crypto miners and Remote Access Tool (RAT) are accompanying the spoofed emails that steal user credentials, captures the screen and exfiltrates data from the victim’s computer.
These resort to activities outlined under Cyber terrorism and has specific provisions covering areas of DDoS attacks, unauthorised access, introduction of computer contaminant files that has the potential to cause harm to persons, property or data theft (India code, 2011). The Modus Operandi fits in the perimetric definition of Terrorism quoted as “an unlawful use or threatened use of force or violence by a person or an organised group against people or property with the intention of intimidating or coercing societies or governments, often for ideological or political reasons”(Benoji, 2004). The attack is predefined, the targets are specifically set. The objective is to damage target centric entities such as politics or military and defence infrastructure, thereby causing fear amongst people. Under the provisions of the IT Act, 2000, such activities are punishable with imprisonment with a possibility of extension for life (India code, 2011).
Cyber-attacks from the past
The WannaCry ransomware attack shut systems in more than 80 NHS organisations in the UK (2017) making the healthcare vulnerable to handle emergency cases. Data was hijacked and a ransom against the data was demanded (Comptroller and Auditor General, 2018). Similarly, NotPetya attack devastated Merck’s global network via a server in its Ukraine office. It wiped data from the computers of the banks, energy firms, airport and the government draining more than $10 billion overall.
In July 2020, Canada, the UK and the US accused hackers from Russian Intelligence for a cyber-attack with an intention to steal information related to Covid-19 vaccine. During the same time, the UK believed that Russia had attempted to steal and leak documents concerning the UK-US free trade agreement thereby interfering in their 2019 general elections.
In the first quarter of 2020, a group of Chinese hackers targeted 75 industries globally covering every sector of the economy. The Cyber Espionage campaign aimed at establishing backdoors for spying purposes by penetrating into vulnerabilities of Zoho Manage Engine Desktop Central, Cisco RV320 routers and Citrix Application Delivery Controller (ADC) (Scott Ikeda, 2020).
A social engineering attack which began in the Philippines in 2000, later spread to Hong Kong- Europe and the USA in one day. The subject of the email read “ILOVEYOU” and included an attachment “LOVE-LETTER-FOR-YOU.TXT.vbs”. This worm infected about 10% of computers that were connected to the internet and a damage of $5.5 billion. Data theft, gaining control over the systems and collecting sensitive information of the internet users were amongst the intentions of the cybercriminal (Nizamettin Aydin).
About 4.1 billion records in the first half of 2019 globally are exposed to data breach, 71% of these breaches were financially motivated while the remaining intended cyber-espionage (Verizon, 2020). About half of the total breaches came from phishing and social engineering activities. Research reveals that every 39 seconds a hacker attacks a system corresponding to about 2,244 times in one day. State sponsored cyber-attacks and organised crime hacking activities are on the rise and potentially will see a dramatic increase in the coming five years (Verizon, 2020). It will not only cause damage and exploitation of data but also be responsible for financial thefts, embezzlement, frauds, post-Covid normalcy to business and theft of intellectual property.
Prevention: Guidelines to survive the Phishing attack
Tips to mitigate the risks that you or your company may be exposed to in the cyberspace are as follows: (Directorate General Central Industrial Security Force, 2020; Indian Computer Emergency Response Team, 2020; Larsonus, 2019).
- Do you know who sent the email? (hover on ‘From:’ field to check). Recognize business emails by visiting their websites directly.
- Did the email come from a government agency or law enforcement (It is very unusual)?
- Do not click on any attachments from unexpected emails or from known contacts. Visit the official websites directly through your browser.
- Scan for ‘remove suspicious email attachments. Check for the attachment extension, block the following extensions: ‘.exe, .pif, .tmp, .url, .vb, .vbe, .scr, .reg, .cer, .pst, .cmd and more”.
- Install a pop-up blocker.
- Fact-check with the content in the email using general google search, for example: If the email reads “ ‘Free Covid-19 test for residents of India’, perform a general google search with the same keywords, if the information is true you will find authentic sources, else there will be many links which will alert you.
- Do not share personal information with unnecessary websites, do not register for ‘too good to be true’ offers.
- Update spam filters to keep your device up to date.
- Spelling errors, alignment issues and irregular text are red flags.
- Encrypt the attachments that you send, maintain good level of privacy while sending emails.
Cyber Security is a priority
- Invest in a good antivirus, antimalware, firewall or opt for a complete internet solution. Configure the software to these settings:
- Specify which files and folders to scan regularly, scan for riskware
- Owner (to restrict access to the tool)
- Real-time email scanning and file protection.
- Scan infectable file types (based on file extensions like .exe, .bin, .com etc.)
- Ransomware and self-protection
- Keep your software updated
- Passwords
- Use a strong password with a combination of the following:
- At least ONE uppercase alphabet
- At least ONE lowercase alphabet
- At least ONE numeric
- At least ONE special symbols “!@#$%^&*_” Example: !Want2beS@fe_4m@Cyb3r_@tt@ck.
- Do not repeat your passwords.
- Use password managers like KeePass, Dashlane or LastPass.
- Use a strong password with a combination of the following:
- Consider Two-factor authentication wherever possible.
- Avoid sharing any form of personal information on social media.
- Use a VPN (Virtual Private Network) to protect your home network. It will encrypt all the traffic leaving your device until it reaches its destination. Paid VPN services are recommended.
- Verify the payment sources before initiating any transactions online.
Prevention measures for Organisations in Cyber-attack
Organisations are prone to the threats of a cyber-attack. They must include data ethics, privacy and security as integral elements of their work agenda (Palmer, 2016). Below is a checklist for organisations to prevent a cyber-attack:
Prepare
- Have strong IT policies, back up your data frequently.
- An appropriate budget for cyber security, this step is often neglected but later repented.
- Consult cyber security experts around the verticals of your company network.
- Identify valuable information that you need to protect, it could range from client data, IPR’s or trade secrets.
- Perform critical risk assessments and carry out threat analysis.
- Identify the types of cyber-attacks your organisation can be prone to.
- Create a backup emergency response plan.
- Consider implementation of tasks to people, identify what happens to the processes and how you can make use of technology to assist during an attack.
- Cross train your employees on areas concerning their privacy, digital security with special attention on the organization’s safety in the cyber space.
Respond
- Identify cyber-attacks.
- Analyse available information, determine what has happened.
- Investigate assets, address unusual problems, recover systems.
- Monitor system logs and alerts.
- Contain the attack by blocking unauthorised access, malware sources and by isolating systems.
- Gather and preserve all retrieved information in different forms: Screen shots, screen recordings, notes, reports etc. Adhere to the guidelines on Computer Evidence laid out by Association of Chief Police Officers (ACPO, 2012). Digital Forensic Investigation
Review
- Report the incident to relevant stakeholders and service providers.
- Conduct a post-incident review.
- Investigate more in depth and identify the attacker, the origins and follow up regularly to avoid relapse of a similar cyber-attack.
Checklist for the victim
- Do not panic.
- If you have downloaded a suspicious attachment, disconnect from the internet immediately.
- Reboot your device by turning it off and on. Press F8, it will open ‘Advanced boot options’ menu.
- Choose “Safe mode with Networking” while you remain disconnected from the internet.
- Delete temporary files and the downloaded attachment.
- Run an antivirus, antimalware scan on your system.
- Reboot your PC to normal mode once the virus is removed.
- Change your passwords.
- Backup your data.
- Keep all logs of the conversation, payment receipts etc. for investigation.
- Log out from all social media accounts from all devices.
- Mark the email ‘spam’, do not open it.
- Report.
Incident Response guidelines for the Investigation and Cyber Security Agencies
Authorised agencies must follow the NIST guidelines for digital forensic investigations (Kent et al., 2006): Collection, Examination, Analysis and Reporting. One can also opt for IDFPM (M.D. Kohn, M.M. Eloffb, 2013) or the SRDFIM model (Agarwal and Gupta, 2011). Usually in any investigation, all these steps run parallel to each other. It is up to the investigator to strategize which step follows the precursor. Nonetheless, advice the client on basic cybersecurity practices, block financial accounts and try to recover their systems and data.
Collection
This step is inclusive of Preparation, Identification, Collection, Packaging and Preservation of evidence.
- Carry out a critical assessment of what has happened.
- Record case logs, conversational evidence obtained from the victim. Preserve the evidence.
- Identify the type and source of attack.
- Correlate to similar attacks.
Examination
This phase includes responding as well as management of the incident.
- Examine the acquired date from the collection phase.
- Extract the data as deemed relevant to the case.
- Secure the network by implementing temporary firewalls, report to the internet service provider to block traffic or other measures as determined useful to block the activities of the cybercriminal.
- Perform necessary measures to stop the spread of the malicious software.
- Conduct network forensics to identify active malware in the client’s environment.
- Conduct host forensics to understand how many systems have been compromised.
Analysis
This phase answers the (5WH) questions about the cyber-incident.
- What happened?
- Who did it?
- When did it take place?
- Where did it happen?
- Why did it happen?
- How was the incident organized?
- Manoeuvre your investigation based on the evidences procured.
Reporting
- Present your investigation findings in a clear and concise format.
- Include tools and techniques used from the collection phase till the analysis phase.
Note: If you are a non-governmental investigation agency, it is recommended to report at the local law enforcement. Depending on the kind of loss that has occurred, a First Information Report (FIR) will be required to approach further remediation procedures. It will also help to gather data from similar attacks, formulate statistics and provide a bigger picture of the incident. Perhaps, this step is very essential to make any public notifications regarding the cyber-attack (Crowdstrike).
Conclusion
Individuals and organisations must emphasise on the importance of privacy, data security and safeguard themselves against potential cyber-attacks. Today, the major threat is from the Chinese hackers, tomorrow it will be someone else. This article has stressed on the importance of maintaining cyber hygiene. The tips and checklists provided here form a basic outline of how cyber incidents can be managed.
It is not just the Chinese hackers that pose a threat to our privacy, especially looking at a sharp increase in phishing attacks since January 2020. Every internet user needs to know the basic cyber security guidelines along with the trending threat landscapes. The damage a cyber-attack can cause is immeasurable. INTERPOL’s Cyber hygiene campaign states that internet users must self-isolate their data, practice social distancing from unknown email senders, avoid contact with any suspicious attachments and always clean their devices (Interpol Cybercrime Directorate, 2020). Digital Forensic Investigation




Pingback: How to report a Cybercrime | Computer Forensics | SURANA & SURANA
Sallie
February 15, 2021 at 11:27 pmMy spouse and I stumbled over here coming from a different web
page and thought I might as well check things out.
I like what I see so i am just following you.
Look forward to exploring your web page for a second time.
Feel free to visit my webpage buy cbd gummies
Corrine
February 21, 2021 at 6:41 pmI love it when folks get together and share views.
Great website, stick with it!
Here is my blog post: buy CBD
Roland
February 21, 2021 at 9:22 pmThis information is worth everyone’s attention. When can I
find out more?
Feel free to visit my webpage: CBD oil