First response: Computer Forensics

By Dr. Vinod Surana
In the electronic era, information is left behind as digital footprints in the cyberspace. The trail of digital evidence is searched, identified and analyzed to link and reconstruct the chain of events. Forensic Investigation of cybercrime cases are complex and depends on evidence identified, recovered and reasoning. The first responder is the first person to arrive at the scene and can even be a complainant to the crime. Once the physical boundaries or electronic scope of the crime are identified, the role of the first responder is to protect the scene and the devices (ex: in a physical computer crime scene, if a laptop screen is on the responder must take photographs in an effort to protect what is on the screen before the battery dies. First responders should not alter or touch anything within the scene and must ensure that nobody enters or leaves the scene. Alternatively, if while browsing you come across an indecent image depicting children in inappropriate or sexual positions, as a first responder you must document every evidence. take screenshots, photographs, video clips and note down the URL from the browser, helping law enforcement use it later as evidence and reconstruct the crime.
Digital evidence is sensitive – volatile and improper handling can irrevocably modify it. Protocols must be meticulously followed to optimize evidence acquisition and extraction and minimize errors.
Computer Forensics & cybercrime Investigation:
Phases of investigation
In 2002 Carrier defined three basic phases of digital investigation: Acquisition, Analysis and Presentation.
- Acquisition phase: captures the state of the device as it is to be analyzed later. The investigation is uncertain and evidences that may be recovered are unknown – the objective of acquisition is to save all digital values bit by bit. Imaging is done to copy data from the suspect’s device to another trusted device. If special forensic tools like FTK imager are used, they should avoid altering the devices to the extent possible.
- Analysis phase: acquired data is then carefully examined and evaluated to identify valuable evidence. Examination of the files, recovery of deleted files and analysis of the directory contents is a part of this phase.
- Presentation phase: based entirely on legal demands and procedures. Corporate laws, privacy laws and other legal constraints are considered. Report is presented in a legal format of a witness statement (Carrier, 2002).
Table 1 shows comparison between various Digital Forensics Models and e-Discovery processes. The stages overlap amongst each other, and It is up to the investigator to evaluate which process fits best depending upon the type of investigation and the source of evidence. Figure 1 illustrates a standard investigation process.Table 1: Comparison between digital forensic process models and e-Discovery process (source: (Carrier, 2002; Carrier and Spafford, 2003; Casey Eoghan, 2010; EDRM.net, 2014; M.D. Kohn, M.M. Eloffb, 2013)
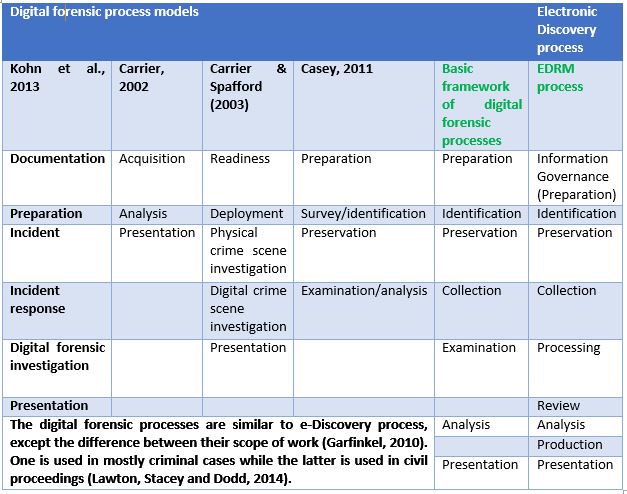
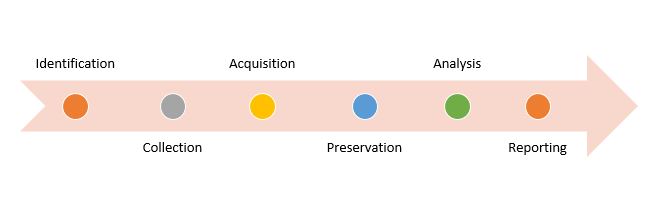
Figure1: Investigation model for Digital Forensic Practitioners and Cybercrime Investigators.
Identification
In this phase, preliminary information is gathered prior to collecting the digital evidence. Questions like what, where, how, when, why and who will help the investigator on how to proceed with the case. The investigator must identify the type of evidence that he is looking for and the possible location of evidence. For example: if there is a fraudulent transaction related cybercrime, the investigator must identify evidence related to transactions, statements, account details, etc. (Carrier and Spafford, 2003; Du, Le-Khac and Scanlon, 2017; Mislan et al., 2017).
Collection
Isolating the device from users and networks is important (if the device is a mobile phone, WIFI and mobile network must be diabled). It is possible for data to be wiped off remotely by the criminal – If a laptop or a computer is on, collect volatile evidence with live acquisition techniques. If the device is powered off, volatile data will be lost (ACPO, 2012; CPS, 2014, 2015; Keir Starmer; Jim Barker-McCardle (ACPO), 2010). Documentation of the entire investigation should be carried out parallel to the other phases. Physical characteristics of the device (make, model, colour, unique identification marks, serial numbers, connections and connected devices must be noted.). Documentation should also include the state in which the device was found (standby/on/off) (Robinson, 2016; Sindhu and Meshram, 2012). Documents must be accompanied by photographs, videos, hand drawn sketches and written notes. Seizure warrants must be implemented if the device needa to be taken for analysis (Agarwal and Gupta, 2011).
Acquisition
Depending upon the type of cybercrime, proper tools and techniques are identified beforehand. Acquisition begins by performing forensic imaging or cloning of the memory devices, an exact copy of the original is created, and a cryptographic hash value is calculated to prove integrity and authenticity of the imaged content. Logical and physical extraction procedures are performed with tools like EnCase, FTK Imager, XRY, Win hex. The entire process must be documented including hardware, software and tools used and the procedure must be replicable by a third party.
Preservation
The integrity of the evidence must be protected at all phases, remaining free from modifications. Chain of custody must be maintained (Badiye Ashish, Kapoor Neeti, 2020; Ballou et al., 2013; Edward J Apple, 2011; Obbayi Lester, 2019)(Figure 2).
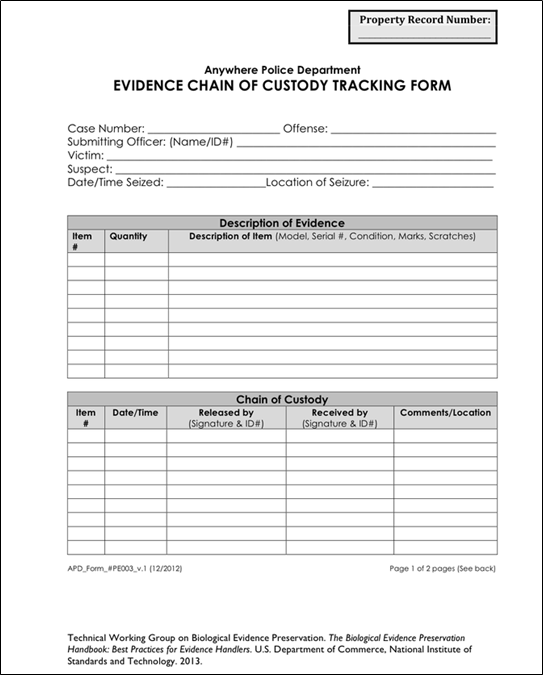
Figure 2: Chain of Custody template (Ballou et al., 2013)
Analysis on Digital investigation
Examination of the digital evidence is followed by interpretation phase. During this phase, the evidence is extracted, data is analyzed and the investigator reconstructs the crime (Van Baar, Van Beek and Van Eijk, 2014; K. Sindhu and B. Meshram, 2012; Robert André Furuhaug, 2019). The goals of the investigation identified in the first phase will guide the search sequence for evidence in this phase. Network, browser, email, social media analyses and cloud, image and video forensics are conducted.
How to report a Cybercrime
The final stage is to communicating the analytic findings. Reports must include case logs, chain of custody, written notes, sketches, photographs, videos and other technical report attachments extracted from forensic tools as appendices. The report must include the aims of investigation, step by step log of every stage, details about the investigator in-charge, and forensic examiner’s qualifications and scientific facts to back his theory or hypothesis (Department of Justice and Unit, 2015; Du, Le-Khac and Scanlon, 2017; Tully, 2012).
What should I do in case I am a victim to Cybercrime?
The Government of India launched a portal to facilitate reporting of cybercrime cases with a focus on those committed against women and children. 2018 saw a leap to 27,248 cybercrimes reported in India – an 86% rise compared to its previous four-week period (Soumik Ghosh, 2020). Cybercrime related complaints can be registered at cyber cells (30 cyber cells around the country). Per Section 154 of the Code of Criminal Procedure, complainants may register irrespective of the location of the crime (Ministry of Home Affairs, 2019a). This is referred to as a ‘Zero FIR’ to accelerates quicker investigations.
As an Organisation (Cyberattacks or vulnerabilities)
The national nodal agency called CERT-In (The Indian Computer Emergency Response Team) oversees organisation targeted computer attacks and advices organisations on how to deal with such attacks (Indian Computer Emergency Response Team, 2020). Cases dealing with Business Email Compromise and data breaches can be reported at the ‘Reporting’ section of their website (https://www.cert-in.org.in/) and following the ‘Incident Report’ protocol. For cyber security incidents one can contact CERT-In Incident Response Helpdesk at incident@cert-in.org.in or call +91-11-24368572 or +91-1800-11-4949 (toll-free). It is recommended to encrypt sensitive information if communicating via email.
CERT-In runs under the patronage of Ministry of Electronics and Technology, Government of India and handles violations related to unauthorised access, DDoS attack, Data breach or email-related security issues, spamming, mail bombing etc. (Indian Computer Emergency Response Team, 2020).
As an Individual
To report a cybercrime, it is vital that all evidences are recorded in forms of photographs, screenshots, videos that can assist an investigation. In case of a phishing fraud or financial fraud the complainant must have evidence of money transfer, email conversations, email header, mobile number, website details, URL and any other relevant evidence. Evidence size is capped at maximum 5 MB, requiring compression if files are larger (Ministry of Home Affairs, 2019a).
Complaints are to be reported on https://cybercrime.gov.in/, the national portal for issues pertaining to digital crimes. Information provided by an individual on the portal is processed by law enforcement. The emergency helpline number (155260) is available between 9:00am to 6:00pm.
Registered complaints can contact the Grievance Officer if there are no appropriate response is received; a State-wise list of nodal officers can be found on https://cybercrime.gov.in/Webform/Crime_NodalGrivanceList.aspx. Using the ‘anonymous’ option, the complainant is not required to reveal his/ her identity – predominantly useful in cases of child pornography, child sexual abuse material, gang rape or sexually abusive content. Crimes related to women and involving children are given due importance and priority while registering on the portal too (Ministry of Home Affairs, 2019a). For other types of cybercrime, refer figure 3 (Ministry of Home Affairs, 2019b).
It recommended to use the ‘Report and Track’ option – your email id and mobile number will be registered, followed by an OTP for authentication. Once complaint is registered, complaint ID number will be allotted, a copy of complaint can be downloaded and an acknowledgement message will be sent to the registered mobile number and email address.
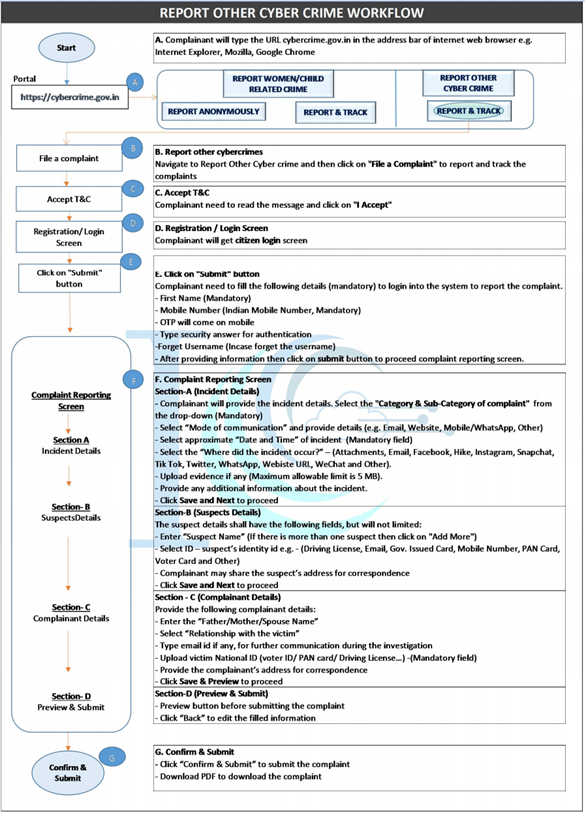
Figure 3: The flowchart to report other types of cybercrime on the national portal (India) (Ministry of Home Affairs, 2019b)
Computer crimes : Conclusion
Rapidly emerging and ever-evolving cyberspace activities pose a continuous stream of new legal questions. The rapid stream of change alongside the public’s increasingly enduring reliance on technology and cyberspace necessitates instilling public awareness of the current provisions of the IT Act. New technologies have direct or indirect impact upon cyber laws and the IT Act must incorporate newer reforms. First responders & investigators must equipped with up-to-date knowledge, pertinent training and resource to adequate address cyber issues.
References
ACPO (2012) ‘Association of Chief Police Officers (ACPO) The Good Practice Guide’, Acpo, (March) London, United Kingdom Available at: https://learningedge.edgehill.ac.uk/bbcswebdav/pid-2746223-dt-content-rid-13602935_1/courses/2018_CIS3144/ACPO_Good_Practice_Guide_for_Digital_Evidence_v5.pdf (Accessed: 20 October 2020).
Agarwal, A.A. and Gupta, M.M. (2011) Systematic Digital Forensic Investigation Model.
Van Baar, R.B., Van Beek, H.M.A. and Van Eijk, E.J. (2014) ‘Digital Forensics as a Service: A game changer’, Digital Investigation, 11(SUPPL. 1) Elsevier Ltd, pp. S54–S62.
Badiye Ashish, Kapoor Neeti, M.R. (2020) ‘Chain of Custody (Chain of Evidence) [Updated 2019]’, StatPearls [Internet]. Treasure Island (FL): StatPearls Publishing, (Jan 2020), pp. 1–11.
Ballou, S., Stolorow, M., Taylor, M., Bamberger, P.S., Brown, L., Brown, R., Burney, Y., Davenport, D., DePalma, L., Williams, S., Jones, C., Keaton, R., Kiley, W., Latta, J., Kline, M., Lanning, K., LaPorte, G., Ledray, L.E., Nagy, R., Ostrom, B.E., Schwind, L. and Stoiloff, S. (2013) The biological evidence preservation handbook : best practices for evidence handlers ; technical working group on biological evidence preservation. Gaithersburg, MD. Available at: 10.6028/NIST.IR.7928 (Accessed: 15 October 2020).
Carrier, B. (2002) Open Source Digital Forensics Tools.
Carrier, B. and Spafford, E.. (2003) ‘Getting Physical with the Investigative Process’, International Journal of Digital Evidence, 2(2), pp. 1–20.
Casey Eoghan (2010) Handbook of digital forensics and investigation. London.
CPS (2015) ‘Expert Evidence’, in Expert evidence. First. London, United Kingdom: CPS, pp. 1–68. Available at: https://www.cps.gov.uk/sites/default/files/documents/legal_guidance/expert_evidence_first_edition_2014.pdf (Accessed: 20 October 2020).
CPS (2014) ‘The Criminal Procedure Rules’, in London, United Kingdom: Crown Prosecution Service, pp. 1–5. Available at: http://www.legislation.gov.uk/uksi/2014/1610/pdfs/uksi_20141610_en.pdf (Accessed: 15 October 2020).
Department of Justice, U. and Unit, C. (2015) Best Practices for Victim Response and Reporting of Cyber Incidents. Washington DC: Justice.gov. Available at: http://www.nist.gov/cyberframework/upload/cybersecurity- (Accessed: 8 November 2020).
Du, X., Le-Khac, N.-A. and Scanlon, M. (2017) ‘Evaluation of Digital Forensic Process Models with Respect to Digital Forensics as a Service’
EDRM.net (2014) ‘Electronic Discovery Reference Model’, EDRM.net, 3, p. 2014.
Edward J Apple (2011) Internet Searches for Vetting, Investigations, and Open-Source Intelligence. Florida, USA: CRC Press.
Garfinkel, S.L. (2010) ‘Digital forensics research: The next 10 years’, Digital Investigation, 7(SUPPL.) Elsevier Ltd, pp. S64–S73.
Indian Computer Emergency Response Team (2020) CERT-In Advisory CIAD-2020-0040., Ministry of Electronics and Information Technology, Govt of India Available at: https://www.cert-in.org.in/ (Accessed: 8 November 2020).
K. Sindhu, K. and B. Meshram, B. (2012) ‘Digital Forensics and Cyber Crime Datamining’, Journal of Information Security, 03(03) Beijing, China, pp. 196–201. Available at: 10.4236/jis.2012.33024 (Accessed: 9 November 2020).
Keir Starmer; Jim Barker-McCardle (ACPO) (2010) Guidance Booklet for Experts. London: Crown Prosecution Service.
Lawton, D., Stacey, R. and Dodd, G. (2014) ‘eDiscovery in digital forensic investigations eDiscovery in digital forensic investigations eDiscovery in digital forensic investigations’, (32)
M.D. Kohn, M.M. Eloffb, J.H.P.E. (2013) ‘Integrated digital forensic process model: Library resources’, , pp. 1–13. Available at: http://eds.a.ebscohost.com.ezproxy.leedsbeckett.ac.uk/eds/detail/detail?vid=54&sid=8bdded0a-6b56-4544-83f9-c4dccefbeeb9%40sessionmgr4010&hid=4213&bdata=JnNpdGU9ZWRzLWxpdmUmc2NvcGU9c2l0ZQ%3D%3D#AN=S0167404813000849&db=edselp (Accessed: 5 November 2020).
Ministry of Home Affairs (2019a) User Manual for National Cybercrime Reporting Portal. Available at: https://cybercrime.gov.in/UploadMedia/MHA-CitizenManualReportCPRGRcomplaints-v10.pdf (Accessed: 10 November 2020).
Ministry of Home Affairs (2019b) Citizen Manual for National Cybercrime Reporting Portal.Government of India (ed.) Delhi: Cybercrime.gov.in. Available at: https://cybercrime.gov.in/UploadMedia/MHA-CitizenManualReportOtherCyberCrime-v10.pdf (Accessed: 10 November 2020).
Mislan, R., Goldman, J., Debrota, S., Rogers, M. and Wedge, T. (2017) ‘Computer Forensics Field Triage Process Model’, The Journal of Digital Forensics, Security and Law, 1(2)
Obbayi Lester (2019) Computer Forensics: Chain of Custody [Updated 2019]., Infosec Institute Available at: https://resources.infosecinstitute.com/category/computerforensics/introduction/areas-of-study/legal-and-ethical-principles/chain-of-custody-in-computer-forensics/#gref (Accessed: 17 October 2020).
Robert André Furuhaug (2019) Open Source Intelligence Methodology. School of Computer Science and Informatics ,University College Dublin.
Robinson, E.M. (2016) ‘Chapter 3 – Crime Scene Photography’, in Robinson, E. M. (ed.) Crime Scene Photography (Third Edition). Third Edit. San Diego, USA: Academic Press, pp. 61–123. Available at: https://doi.org/10.1016/B978-0-12-802764-6.00003-9 (Accessed: 24 October 2020).
Sindhu, K.K. and Meshram, B.B. (2012) ‘Digital Forensic Investigation Tools and Procedures’, International Journal of Computer Network and Information Security, 4(4) Mumbai, India, pp. 39–48. Available at: 10.5815/ijcnis.2012.04.05 (Accessed: 20 October 2020).
Soumik Ghosh (2020) How to report a cybercrime in India | CSO Online., CSO India Available at: https://www.csoonline.com/article/3564601/how-to-report-cybercrime-in-india.html (Accessed: 10 November 2020).
Tully, G. (2012) ‘Codes of Practice and Conduct’, (1), pp. 1–15. Forensic Science Regulator, United Kingdom,https://www.gov.uk/government/uploads/system/uploads/attachment_data/file/355448/FrequencyDatabasesReportingGuidance.pdf (Accessed 09 November 2020).




Debora
August 17, 2022 at 3:45 amI’m not that much of a online reader to be honest but your
sites really nice, keep it up! I’ll go ahead and bookmark
your website to come back down the road. Cheers
Feel free to visit my blog; Generic cialis tadalafil
Esperanza
September 18, 2022 at 3:32 pmYes! Finally something about online pharmacies.
Here is my site: online medicine tablets shopping
Dustin
September 24, 2022 at 12:03 amThank you for the good writeup. It in fact was a amusement account it.
Look advanced to more added agreeable from you! However, how
could we communicate?
My web blog … can you buy cialis online
AnthonyRep
July 25, 2023 at 9:21 pmAll in all, Crypto pump signals for Binance is a trusted source of information about cryptocurrency pumps Crypto pump signals that provides accessible and professional assistance for traders who wish to use this strategy in their trading.